Obliging regulations have the potential to ensure safety within communities – yet they can also introduce doubt. The Cyber Resilience Act (CRA) exemplifies this duality. The reception within the open-source community and tech industry has been varied, spanning from concern to optimism.
The CRA, a directive originating from the European Union, targets enhancing the security of products with digital components by imposing stringent cybersecurity, documentation, and vulnerability disclosure standards within the IT sector. It encompasses a broad spectrum of entities such as developers, distributors, manufacturers, and retailers of hardware, software, applications, and other digitally connected products.
“The CRA seeks to protect consumers and businesses engaging with products or software involving digital elements. It aspires to eliminate inadequate security features by enforcing mandatory cybersecurity protocols for manufacturers and retailers, ensuring protection throughout a product’s life cycle.”
EU Cyber Resilience Act
The act ensures harmonized standards during the product launch of items containing digital components, outlines cybersecurity prerequisites across all stages of the product life cycle, and mandates a duty of care throughout the product’s lifespan.
The Core Objectives of the Cyber Resilience Act
The Cyber Resilience Act is designed with four key objectives:
- Drive manufacturers to enhance product security from inception through the entire life cycle.
- Establish a cohesive cybersecurity framework for hardware and software producers.
- Increase transparency regarding security properties of products with digital elements.
- Enable secure utilization of products with digital components by businesses and consumers.
These objectives necessitate manufacturers to prioritize the security of devices pre- and post-production, ensure compliance with new EU standards for publicly available hardware and software, divulge comprehensive information regarding product design and components, and promptly report critical vulnerabilities.
Implications of the Cyber Resilience Act
- Stricter security standards must be met, covering design, updates, and the entire product lifecycle.
- New requirements encompass risk assessment, documentation access, compliance evaluation, and vulnerability disclosure.
- Compliance deadlines loom, with severe penalties for non-adherence to the legislation.
Enhanced Cybersecurity Standards
The CRA introduces rigorous EU-mandated standards for developers, manufacturers, importers, and distributors of software and digital products. The criteria include minimizing attack surfaces, ensuring secure product updates, and maintaining clear, accessible documentation.
- Optimal security of created products is mandated to limit potential attack vectors.
- Devices are required to possess robust security frameworks, enabling encrypted data transmission and resistance to unauthorized access.
- Facilitation of security updates and rollbacks is necessary, along with comprehensive risk assessments and conformity validation.
Design, Documentation, and Compliance Requirements
The CRA outlines four primary obligations:
- Risk Assessment
- Documentation
- Conformity Assessment
- Vulnerability Reporting
I. Risk Assessment
Manufacturers are obliged to conduct thorough cybersecurity risk assessments to ensure products are devoid of exploitable vulnerabilities and promote a ‘secure by default’ configuration.
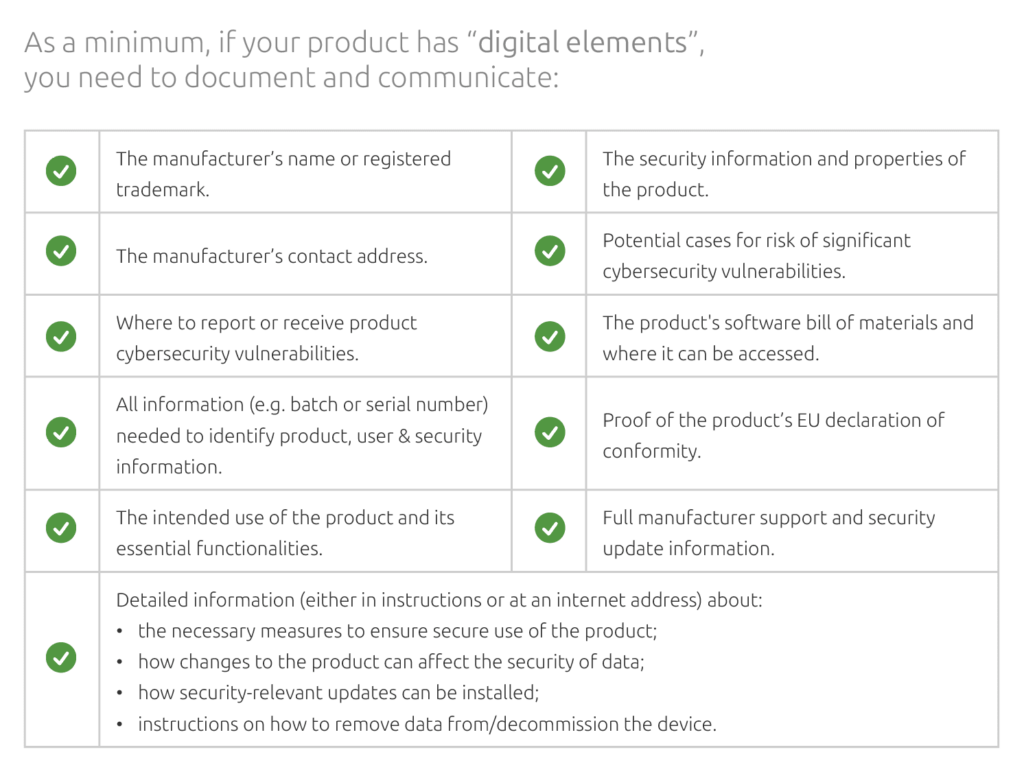
II. Documentation
New documentation guidelines necessitate providing detailed descriptions of design processes, cybersecurity risk assessments, EU standards compliance lists, signed Declarations of Conformity, and Software Bills of Materials.
III. Conformity Assessment
Products are categorized based on risk level, with Class I & II products requiring evaluation by third-party authorities for compliance confirmation.
IV. Reporting and Vulnerability Oversight
Producers are mandated to promptly report vulnerabilities to the European Union Agency for Cybersecurity (ENISA) and maintain meticulous documentation on product vulnerabilities and updates.
- Identification and documentation of vulnerabilities within the product are vital.
- Secure updating mechanisms are critical, alongside immediate vulnerability fixes and transparent public disclosure policies.
Preparation for the Cyber Resilience Act
Engage with Key Teams and Absorb the Legislation
Collaborate with legal, compliance, and engineering teams to comprehend the implications of the CRA and identify relevant regulatory scopes for your organization.
Prioritize Documentation and Transparency
Transparently showcase your product’s origin and safety features through detailed documentation accessible to users and regulatory bodies.
Reassess Cybersecurity Protocols
Use the CRA as a catalyst to review existing cybersecurity measures, ensuring compliance and fortification of your products.
Implement Robust Vulnerability Reporting Procedures
Establish clear protocols for reporting vulnerabilities to avoid regulatory penalties and to comply with CRA guidelines.
Cultivate operational processes that adhere to CRA’s demands and anticipate your product’s classification to align with the evolving cybersecurity landscape.
Comprehensive Documentation and Compliance Checklist
Understand the documentation requirements imposed by the CRA to effectively communicate your product’s cybersecurity details.