Introducing the latest entry in our series focusing on transparency within the Microsoft Security Response Center (MSRC). This ongoing discourse delves into our dedication to furnishing thorough vulnerability details to our clientele.
At MSRC, our primary objective is safeguarding our customers, communities, and Microsoft itself from both existing and emerging security and privacy threats. In our prior blog entry, we scrutinized the foundational causes behind vulnerabilities cataloged with CWEs. This article delves into the documentation of a fresh category of vulnerabilities: Cloud Service CVEs.
The CVE program, celebrating its 25th anniversary this year, has always seen active participation from Microsoft. With time, the industry has undergone significant transformations, with cloud-based services becoming increasingly integral to our everyday routines. In the past, Cloud service providers (CSPs) refrained from divulging information about vulnerabilities identified and resolved in cloud services unless customer intervention was deemed necessary. There was a common notion that if customers did not require updates, then no additional information was warranted to aid them in maintaining security. However, with the industry’s evolution, we now comprehend the importance of transparency. Consequently, we hereby declare our intention to assign CVEs to critical vulnerabilities in cloud services, irrespective of whether customers need to apply a patch or implement other measures for safeguarding themselves.
As our sector progresses and steadily transitions to cloud-based services, it’s imperative that we are forthright about significant cybersecurity vulnerabilities discovered and rectified. By openly disseminating information regarding identified and rectified vulnerabilities, we empower Microsoft and our collaborators to learn and enhance their practices. This collaborative endeavor contributes to bolstering the safety and resilience of our critical infrastructure.
This commitment aligns harmoniously with the objectives of Microsoft’s Secure Future Initiative (SFI), outlining our engineering priorities. These priorities encompass revolutionizing software development, integrating novel identity protections, and amplifying transparency and expediting vulnerability responses, as vocalized by Charlie Bell, Executive Vice President, Microsoft Security.
The CVE program recently revamped the guidelines providing directives to CVE Numbering Authorities (CNA) such as Microsoft. This shift towards increased transparency is encouraged by these fresh directives. Section 4.2.2.2 mandates:
4.2.2.2 CNAs SHOULD Publicly Disclose and assign a CVE ID if the Vulnerability:
- has the potential to cause significant harm
or
- mandates action or risk assessment by entities beyond the CNA or Supplier.
The presence of “or” between items 1 and 2 holds significance as it urges CNAs to allot CVEs to substantial vulnerabilities, regardless of customer requirements. We prompt all CNAs to evaluate how these new rules impact their products.
MSRC acknowledges that not all customers are inclined to invest effort and time into addressing this fresh classification of CVEs that do not necessitate further action. Consequently, we are enhancing the Security Update Guide and APIs to filter content based on this criterion.
-
A novel column will be featured on the Security Update Guide Vulnerabilities tab to indicate if customer action is needed.
-
The API will introduce a new Notes Type for facilitating the filtering process.
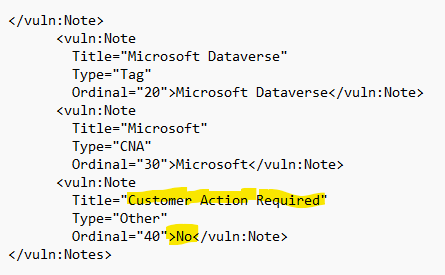
-
Within the CVE.org record, the exclusively-hosted-service tag shall be utilized to signify that no action is necessitated by the customer.
An illustration of this new category is CVE-2024-35260.
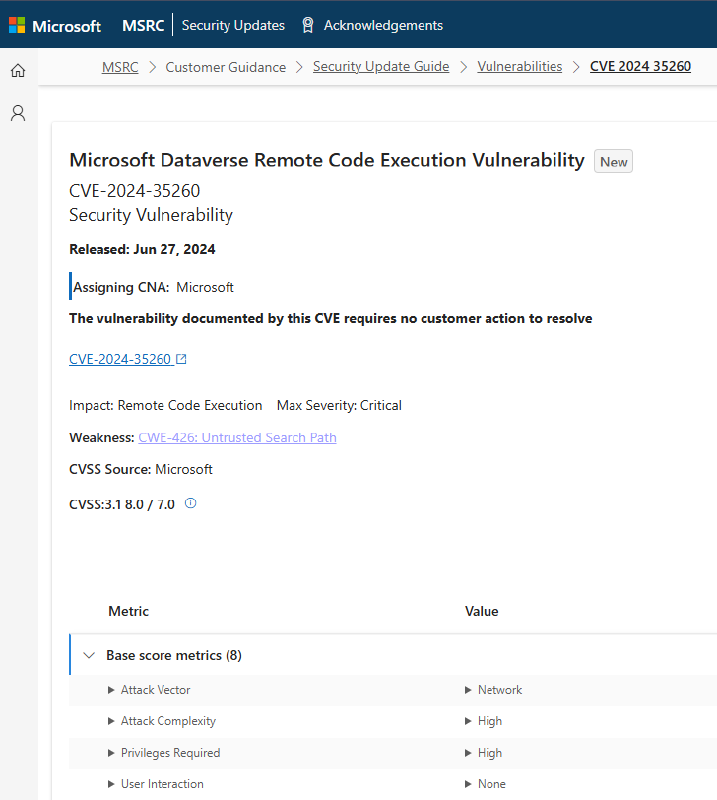
We eagerly anticipate receiving your input, which can be shared by clicking on the rating banner located at the bottom of each CVE page within the Security Update Guide.
Lisa Olson, Senior Program Manager, Security Release