OpenShift safeguarded containers, constructed on Kata Containers, now present the extra ability to operate private containers (CoCo). Covert Containers are containers implemented within a secluded hardware sanctuary safeguarding data and code from authorized users such as cloud or cluster managers. The CNCF Confidential Containers initiative is the basis for the OpenShift CoCo resolution. Further insights on the CNCF CoCo initiative can be found in our earlier post What is the Confidential Containers initiative?
Covert Containers are accessible from OpenShift secured containers launch edition 1.7.0 as a tech glimpse on Azure cloud for both Intel TDX and AMD SEV-SNP. The tech glimpse also consists of support for covert containers on IBM Z and LinuxONE utilizing Secure Execution for Linux (IBM SEL). Upcoming editions will support bare metal installations and additional public clouds.
It’s essential to note that CoCo is an additional characteristic given by OpenShift secured containers, consequently, it’s presented through the OpenShift secured containers operator.
A new operator is also being launched, the secretive compute validation operator, which can validate the reliability of TEEs distantly. In the subsequent blog segment, we will elaborate on this operator and how CoCo utilizes it.
An Introduction to OpenShift Secure Containers
Why is there a necessity for secret containers?
OpenShift protected containers (OSC) grant supplementary seclusion for OpenShift workloads (pods):
- Segregation between workloads: This guarantees that workloads can’t obstruct one another even when given elevated privileges, such as CI/CD workloads that may necessitate elevated privileges. This potential can also be termed pod-sandboxing.
- Isolating the cluster from the workload: This assures that the workload can’t execute any operations on the real cluster like reaching the OpenShift nodes.
Covert Containers (CoCo) extend OSC to tackle a unique form of seclusion:
- Isolate the workload from the cluster: This ensures that the cluster manager and the infrastructure manager can’t view or modify the workload and its data. This affords data in use preservation for your workloads.
Why is this significant?
Currently, there are existing mechanisms to shield your data at rest (encrypting your disk) and data in transit (securing your connection). Yet, there’s a gap in guarding your workload when it’s functioning (data in use), like operating an AI model that signifies your secret formula or transmitting your customer’s confidential data to your LLM for inference. Secret containers address this by protecting your data in use.
Through CoCo, the jeopardy of unauthorized entities accessing your workload data, withdrawing your secrets or intellectual property, or tampering with your application code, is greatly diminished when you set up your workload on infrastructure owned by others.
Covert containers draw on Confidential Computing
Confidential Computing aids in shielding your data in use through leveraging specialized hardware-based solutions. By utilizing hardware, you can design secluded environments possessed by you to help defend against unauthorized entry or alterations to your workload’s data while it’s being executed (data in use). This is notably imperative when managing sensitive information or in regulated sectors.
The hardware employed to establish classified environments consists of Intel TDX, AMD SEV-SNP, IBM SEL on IBM Z and LinuxONE, and more. The obstacle is that these technologies are intricate and demand extensive comprehension to adopt and implement.
Secretive containers seek to simplify matters by offering cloud-native resolutions for these technologies.
Secrecy containers enable cloud-native confidential computing employing a variety of hardware platforms and supporting technologies. CoCo strives to standardize classified computing at the pod level and make its consumption straightforward in Kubernetes milieus. Thus, Kubernetes users can deploy CoCo workloads utilizing their accustomed workflows and tools without necessitating a profound understanding of the underlying covert containers technologies.
By utilizing CoCo, you can deploy workloads on shared infrastructure while lessening the peril of unauthorized entry to your workload and data.
How does this wizardry unfold in reality?
CoCo merges Trusted Execution Environments (TEE) framework with the cloud-native realm. A TEE is instrumental in a confidential computing solution. TEEs are separated environments with enhanced security (e.g., runtime memory encryption, integrity preservation), equipped by confidential computing-eligible hardware. A particular virtual machine (VM) named a confidential virtual machine (CVM) that executes within the TEE lays the groundwork for the OpenShift CoCo resolution.
Let’s now associate this with OSC. OSC sandboxes workloads (pods) deploying VMs, and when utilizing CVMs, OSC now grants covert container abilities for your workloads. When introducing a CoCo workload, OSC sets up a CVM that operates within the TEE granted by confidential computing-eligible hardware, and unrolls the workload inside the CVM. The CVM impedes anybody who isn’t the workload’s rightful proprietor from accessing or even observing what happens within it.
The subsequent depiction shows the connection between a workload (pod) deployed on a CVM that functions inside the TEE rendered in the public cloud hardware or on-prem hardware:
Confidential containers rest on attestation
A pivotal facet of the confidential containers solution, notably in the context of the zero-trust security pattern, is attestation. Ahead of deploying your workload as a confidential container, you require a method to ensure the TEE is trusted. Attestation is the method employed to validate that a TEE, where the workload will execute (e.g., in a precise public cloud) or where you intend to dispatch confidential information, is indeed trusted.
The combination of TEEs and attestation capability allows the CoCo resolution to furnish a credible environment to execute workloads and technically impose the safeguarding of code and data from unauthorized entry by privileged entities.
In the CoCo resolution, the Trustee project (part of the CNCF Confidential Containers initiative) supplies the capability of attestation. It’s accountable for executing the attestation operations and delivering secrets post-successful attestation. For additional facts on Trustee, it is suggested to peruse our former piece, Introducing Confidential Containers Trustee: Attestation Services Solution Overview and Use Cases.
Trustee contains, among others, the ensuing key components:
- Trustee agents: These elements operate within the CVM. This encompasses the Attestation Agent (AA), responsible for dispatching the evidence (claims) from the TEE to prove the environment’s trustworthiness.
- Key Broker Service (KBS): This service acts as the entrance for remote attestation. It directs the evidence (claims) from AA to the Attestation Service (AS) for verification and, upon successful verification, enables the delivery of secrets to the TEE.
- Attestation Service (AS): This service authenticates the TEE evidence.
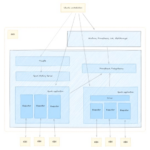
The subsequent diagram unfolds how Trustee components interact in the OpenShift CoCo resolution:
The secretive compute attestation operator
This fresh confidential compute attestation operator is a fragment of the OpenShift CoCo resolution. It facilitates the deployment and administration of Trustee services in an OpenShift cluster.
It supplies a custom resource dubbed KbsConfig to configure the obligatory Trustee services, like KBS, AS, etc. Additionally, it streamlines management of secrets for covert containers.
The ensuing diagram unfolds how this operator links Trustee to OpenShift:
As displayed in the diagram, the confidential compute attestation operator needs to run in a trusted environment to preserve the integrity and security of vital services, like the AS and KBS. These are pivotal for validating and conserving the trustworthiness of the TEE.
When deploying this operator, it is advised to:
- Deploy in an OpenShift cluster running in a trustworthy environment: Employ an existing secured cluster, like your secure software supply chain environment, to grant a credible foundation.
- Integrate prevailing key management systems and link it to the KBS, e.g. through the External Secrets Operator or Secrets Store CSI driver.
Bringing Everything Together
The subsequent diagram reveals a typical deployment of the OSC CoCo resolution in an OpenShift cluster running on Azure while the covert compute attestation operator is deployed in a separate credible environment:
As showcased in the diagram, OpenShift secretive containers utilize a CVM as the foundation and operate inside a TEE. The containers function inside the CVM to safeguard data confidentiality and integrity.
It’s crucial to note the following:
- OpenShift covert containers utilize a CVM to operate inside a TEE to preserve data confidentiality and integrity.
- The Linux guest components are responsible for downloading workload (pod) images and executing them inside the CVM.
- The containerized workload (pod) executing in the CVM, gains from encrypted memory and integrity assurances provided by the TEE.
- Trustee agents run in the CVM, executing attestation and acquiring necessary secrets.
- The cluster where the pod executes is an untrusted environment, the solely trusted components are the CVM and the components operating inside it.
- The covert compute attestation operator operates in a trusted environment different from where the workload (pod) is functioning. This is your trust anchor to validate the trustworthiness of the TEE.
- Attestation validates the trustworthiness of the TEE before the workload executes and can access the secrets.
Recap
OpenShift secretive containers append a potent supplementary layer of security, assisting in ensuring your data remains secure even when in use. This safeguarding of data in use signifies that not even authorized users, like cluster or infrastructure managers, can reach your data without consent. This solution leverages hardware-based TEEs coupled with attestation and key management through Trustee services, all orchestrated by the OpenShift confidential compute attestation operator.
Deployment of the OpenShift CoCo solution mandates utilizing a trusted environment running the confidential compute attestation operator to deliver the attestation and key management services.
OpenShift secretive containers are also designed to effortlessly harmonize with other OpenShift resolutions such as OpenShift AI and OpenShift Pipelines.
In our next piece, we shall delve into the ecosystem adjacent to the covert compute attestation operator and scrutinize practical use cases that underscore the benefits of OpenShift secretive containers.